GARDİYAN: Secure Your Systems with Continuous Monitoring.
Gardiyan optimizes resource usage by monitoring system performance and provides rapid response to security threats, alleviating the workload of IT teams.
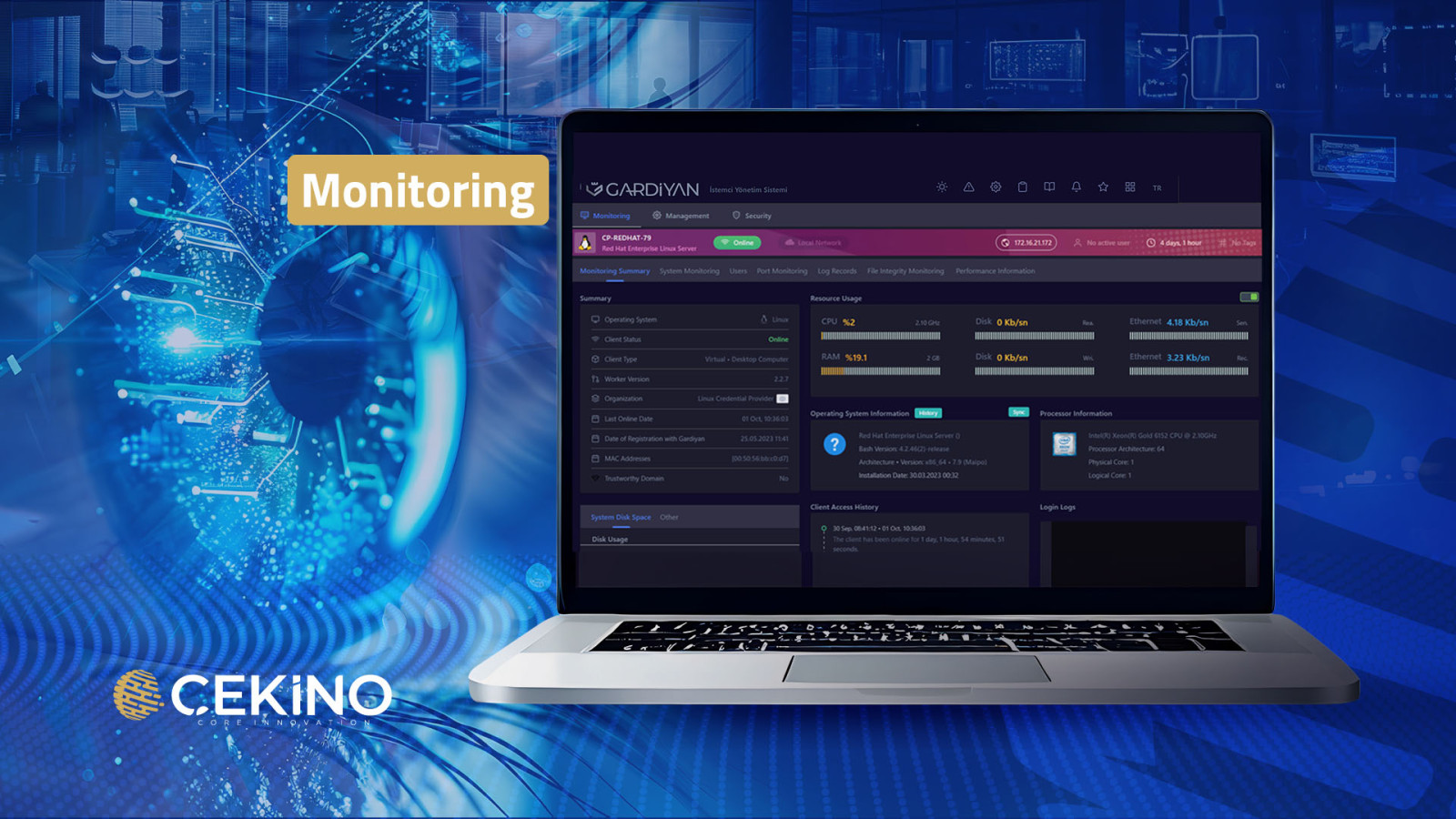

Overview
GARDİYAN offers a comprehensive monitoring solution to keep the performance and security of your system at the highest level. It includes many important functions, from real-time tracking of system resources to logging user activities. By monitoring system performance, it optimizes resource usage and allows you to detect potential performance issues in advance.
GARDİYAN collects and analyzes all the data necessary to ensure the security of your system. With this feature, you can monitor both the activities occurring in the system and respond quickly and effectively to potential security threats. GARDİYAN facilitates system management, lightening the workload of IT teams and ensuring that systems operate continuously in a secure and efficient manner.
Monitoring Summary
Resource Usage
It retrieves processor information, disk read information, memory usage information, and Ethernet information from the client in real time via XMPP (Extensible Messaging and Presence Protocol).
Operating System Information
The operating system information installed on the client is retrieved via XMPP.
Processor Information
This page displays processor information collected from various platforms using XMPP (Extensible Messaging and Presence Protocol).
System Disk Space
This page shows the disk usage details of the client. Disk space usage is a critical metric for the efficiency of our system and the performance of applications.
Client Access History
This page details the times and durations of sessions for clients accessing our system. Access history provides important information about how long clients remained active on the system, their usage habits, and system load times.
Login Logs
Details the login activities performed by specific users. This section includes log records containing usernames and login times.
Speed Test
This page displays the speed test results used to measure the speeds of users' internet and local network connections. The popular Speedtest application is used for internet speed testing, while the iperf tool is used for local network speed testing.
Users
Displays the defined and active user profiles on the client system. The listed users are individuals who can access the system and perform certain functions. Each user's username, display name, and relevant user folder path are detailed.
User Activity History
Shows a log recording significant user activities performed on the client. Records of newly added or deleted users have been logged in the system log at specified dates and times.
System Monitoring
Processor
Contains information about processor usage and the number of cores. This data is obtained and displayed in real-time via XMPP.
Memory
The total, used, and available memory amounts in the system are tracked in real-time via XMPP.
Swap Memory
The usage and capacity of swap memory are also tracked in real-time via XMPP.
Disks
This screen is an interface used to view data on disks and monitor the current storage space. Disk usage information is updated in real-time thanks to instant XMPP connections. This allows users to manage their storage space more effectively and obtain instant information.
Disk IO
This interface monitors input/output operations occurring on the disks of our system in real-time using the XMPP protocol. Disk IO operations show the amount and speed of read and write operations on the disks, which is an important indicator of system performance.
Network
Shows detailed traffic information related to our system's network interfaces. Network traffic includes sent and received packets, as well as potentially faulty and dropped packets. This is monitored in real-time via XMPP.
Users
Displays the session information of active users in the system. Each user's login time and username details are provided, showing who has used the system and when.
Port Monitoring
Notifications
Port notifications summarize activities related to the opening of network ports used by specific applications in your system. Each record indicates which application opened which port on which IP address.
Open Ports
What is intended to be done in the system is the identification and monitoring of open ports used by certain applications and system processes. Monitoring is carried out to continuously check the status of these ports, which are important for system security. Especially for ports with critical functions (such as remote desktop protocol and file sharing ports), this monitoring is done to prevent potential security vulnerabilities and unauthorized access. Additionally, it aims to provide detailed records of which applications are using which ports, offering information about network traffic and resource usage.
Log Records
Remote Desktop Connection Options
Shared & Unshared Connection
These screens are logging interfaces used to record user connection durations and activities. They are designed to document each user’s connection and the operations performed at that time. This provides effective monitoring and management of user activities on the system. The logging system helps quickly identify any security breaches or suspicious behaviors while allowing for transparent examination of user activities.
Client and User Access History
Client Access History
Logging client access history is an important security and management tool that documents how long users interacted with the system. These logs detail the interaction times between the client and the system at specific dates and times. Logging provides system administrators and security experts the ability to monitor and analyze user activities.
Login History
Login logs are an important security and monitoring tool that records when users logged into the system. These logs include a timestamp for each login attempt, allowing system administrators and security experts to maintain detailed control and observation over user access.
Critical Level Records
Documents instances when processor usage reaches critical levels and indicates potential system overloads or performance issues. Logging captures the percentage of processor usage at specific times, allowing for customizable data displays based on user needs, supporting faster and more effective decision-making processes. Regular monitoring of critical data like processor usage is vital for optimizing system performance and detecting potential technical issues early.
Browser History
Browser history logs detail the web activities carried out by users via specific browsers. These logs contain user activities for browser types such as Google Chrome, Firefox, and Microsoft Edge, showing the web pages visited and searches performed in the last 24 hours.
Process and Service Records
Process Records
Process records provide detailed information about specific activities occurring on the system. These records include the names of processes executed by users, the names of users who initiated the process, the duration of the process, the file path where the process was executed, the name of the process file, and the date when the process occurred.
Service Records
Logs the status changes of services in the system and records the moments they are started and stopped. The service records logging screen is designed to provide system administrators detailed control over the operational statuses of services and any changes in the system. Additionally, it is equipped with filtering features that allow users to filter logs based on specific criteria.
Process, Service, Event Log Records
Event Log
The event log logging screen is a logging tool that records various events occurring on the operating system in detail. This screen categorizes security, application, and system-related events, allowing IT professionals and system administrators to monitor them quickly and effectively. Here are the main features and functions of the screen:
Features
- Categorization: Events from different categories such as security, application, and system are listed separately, making it easier to focus on specific types of events.
- Filtering: Logs can be filtered by event type (Error, Information, Warning, Success Audit, Failure Audit) for quick access to the desired information.
- Event Count: The screen lists the last 100 events on the operating system, allowing users to see the most current events and take action on them.
Functionality
- Event Details: Each log contains the timestamp, type, source, and message of the event.
- Real-time Information Provision: The logging screen updates in real-time as events occur, allowing for quick responses to changes or potential issues in the system.
Use Cases
- Security Monitoring: Security-related logs include important security events such as unauthorized access attempts and successful login operations. This information is used to prevent or respond to security breaches.
- System Health: Application and system logs document technical issues such as software errors, system failures, or configuration problems. These logs assist in monitoring system health and troubleshooting.
USB Monitor Settings (BETA)
The USB Monitor Settings screen is a monitoring tool that displays the disk information, connection dates, and file operations occurring within USB devices. This screen logs the usage details of USB devices and changes made to the system. It is used to track data transfers and modifications from USB devices in detail. Monitoring events occurring on USB connections helps in early detection of security risks, such as potential data leaks or malware infections. Additionally, it is valuable for ensuring compliance with appropriate usage policies by keeping a record of the actions performed on USB devices.
Scheduled Tests
The Scheduled Tests screen is a system monitoring tool that shows how specific tasks or tests are performed at designated times. This screen includes details of actions carried out by various operators, including start and end times, results, and relevant observation options.
File Integrity Monitoring
The File Integrity Monitoring screen is a tool that records and monitors changes to files on the system. This screen lists events where files are created, deleted, modified, or moved in detail. By continuously monitoring changes made to the system, it is used to maintain the integrity of critical files and quickly detect unauthorized changes. File integrity monitoring is especially crucial for security, as modifications to files can have direct impacts on system security and operational efficiency. This monitoring tool supports the enforcement of IT security policies and provides proactive protection against potential security breaches.
Performance Monitoring
The Performance Information screen provides daily and weekly data showing how long the system and applications have been active. This screen particularly analyzes the usage durations of operating systems and loaded applications, providing valuable insights to system administrators. It is an important tool for understanding system performance and usage. Information such as client uptime can be considered an indicator of overall stability and reliability in the system. A lack of data regarding system and user applications may indicate low application activity during the relevant time intervals or that activities have gone unrecorded. This information aids in making strategic decisions for the management and optimization of system resources.